D. Description of the Example Architectures#
As indicated in Architecture and Builds, this appendix contains the detailed description of the three example architectures for achieving visibility of TLS 1.3 encrypted network traffic.
Return to Architecture and Builds.
D.1 Description of the Bounded-lifetime DH Key Architecture#
The figure below depicts the high-level architecture components and interactions that achieve visibility of TLSv1.3 traffic using rotated bounded-lifetime ephemeral Diffie-Hellman keys (EDH) on the TLS server. In this approach, the Key Governance Platform generates a new EDH key pair at a designated interval. The key pair is then simultaneously pushed to the TLS server and the real-time decryptor. The post facto analytics platform can query the Key Governance Platform using the TLS server name and connection time (epoch) of the session as parameters to retrieve the EDH server key for decrypting the stored TLS traffic stream. Additional details for this architecture are available in Section 5.2 of NIST SP 1800-37B: Approach, Architecture, and Security Characteristics.
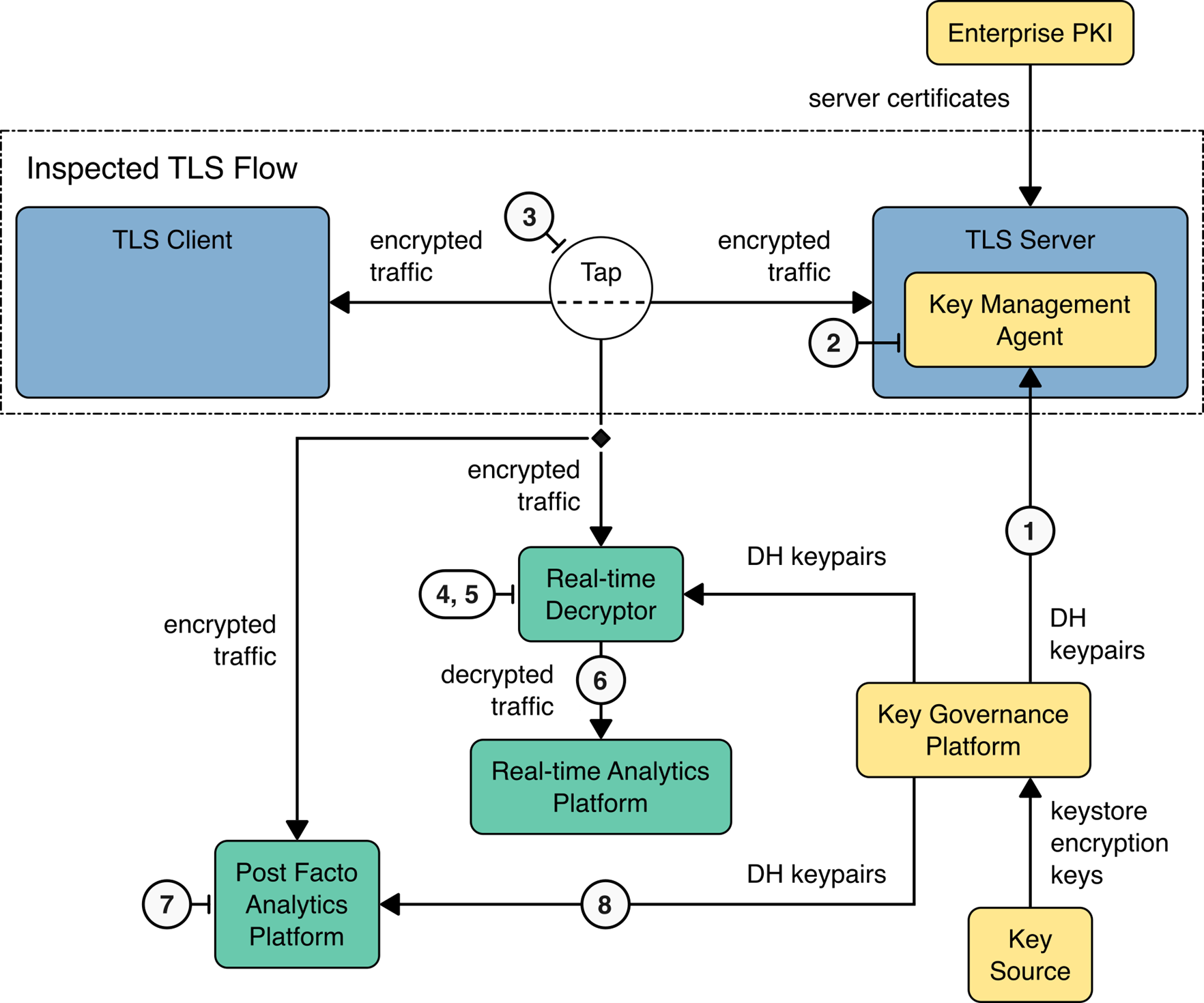
Bounded-lifetime Diffie Hellman Key Architecture#
In the lab build for this reference architecture, software or services used for each of the architecture components can be found in the table below.
Architecture Component |
Collaborator |
Product Information |
|---|---|---|
Architecture Component |
Collaborator |
Product Information |
Enterprise PKI |
DigiCert |
CertCentral Certificate Management Platform |
TLS Client |
Mozilla Firefox Browser |
|
Microsoft Edge Browser |
||
Command-line Email Client & Mozilla Thunderbird |
||
Tap |
VMWare vSphere Distributed vSwitch port mirroring |
|
TLS Servers |
Nginx reverse proxy and containerized Keycloak IdAM application |
|
Nginx reverse proxy and containerized Python test application |
||
MariaDB Database Server |
||
Postfix SMTP Server and Dovecot IMAP Server |
||
Key Management Agent |
Not For Radio |
Encryption Visibility Architecture Encryption Visibility Agent (EVA) Version 0.7.0 |
Real-time Decryptor |
MIRA |
Encrypted Traffic Orchestration (ETO) Version 2.1.0 build 2023.10.24-0009 Virtual Appliance |
Key Governance Platform |
AppViewX |
appviewX Version 2020.3.10 build 55 Virtual Appliance |
appviewX Software Security Module Version 2.6.1 Virtual Appliance |
||
Real-time Analytics Platform |
NetScout |
nGeniusONE Version 6.3.5 build 2416 |
Omnis Cyber Intelligence (OCI) Version 6.3.5 build 2416 |
||
Post Facto Analytics Platform |
vSTREAM ISNG Version 6.3.5 build 946 |
|
vCYBERSTREAM ISNG Version 6.3.5 build 946 |
||
Key Source |
Thales TCT |
Luna Network HSM T-5000 Firmware: Version 7.11.1 FIPS-validated |
Return to Middlebox Architecture. Return to Architecture and Builds.
D.2 Description of the Exported Session Key Architecture#
The figure below depicts the high-level architecture components and interactions that achieve visibility of TLSv1.3 traffic through the export of TLS session keys from the TLS server. In this approach, a Key Capture and Registration Agent installed on the TLS server retrieves the symmetric keys of each TLS session and forwards the key to the Real-time Decryptor which relays the key to the Key Governance Platform. The post facto analytics platform can retrieve the session keys by querying the Key Governance Platform using the client random identifier from the subject traffic stream. Additional details for this architecture are available in Section 5.2 of NIST SP 1800-37B: Approach, Architecture, and Security Characteristics.
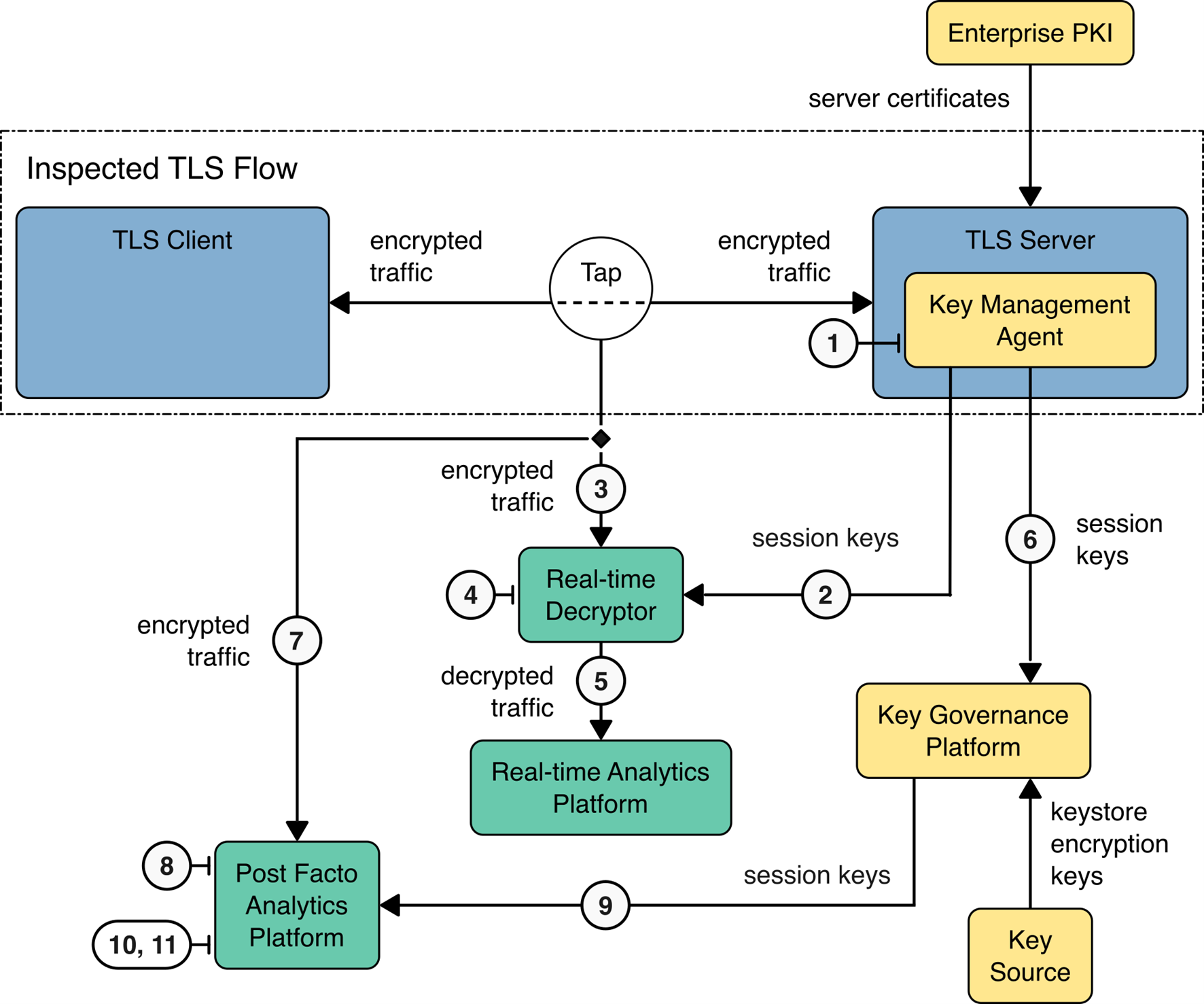
Reference Architecture for Active Break and Inspect Decryption#
In the lab build for this reference architecture, software or services used for each of the architecture components can be found in the table below.
Architecture Component |
Collaborator |
Product Information |
|---|---|---|
Architecture Component |
Collaborator |
Product Information |
Enterprise PKI |
DigiCert |
CertCentral Certificate Management Platform |
TLS Client |
Mozilla Firefox Browser |
|
Microsoft Edge Browser |
||
Command-line Email Client & Mozilla Thunderbird |
||
Tap |
VMWare vSphere Distributed vSwitch port mirroring |
|
TLS Server(s) |
Containerized nginx reverse proxy and Keycloak IdAM application |
|
Containerized nginx reverse proxy and Python test application |
||
MariaDB Database Server |
||
Containerized Postfix SMTP Server and Dovecot IMAP Server |
||
Key Capture and Registration Agent |
Not For Radio |
Encryption Visibility Architecture Encryption Visibility Agent (EVA) Version 0.7.0 |
Real-time Decryptor |
MIRA |
Encrypted Traffic Orchestration (ETO) Version 2.1.0 build 2023.10.24-0009 Virtual Appliance |
Key Governance Platform |
AppViewX |
appviewX Version 2020.3.10 build 55 Virtual Appliance |
Redis database |
||
Real-time Analytics Platform |
NetScout |
nGeniusONE Version 6.3.5 build 2416 |
Omnis Cyber Intelligence (OCI) Version 6.3.5 build 2416 |
||
Post Facto Analytics Platform |
vSTREAM ISNG Version 6.3.5 build 946 |
|
vCYBERSTREAM ISNG Version 6.3.5 build 946 |
||
Key Source |
Thales TCT |
Luna Network HSM T-5000 Firmware: Version 7.11.1 FIPS-validated |
Return to Middlebox Architecture. Return to Architecture and Builds.
D.3 Active Inspection Using a Break and Inspect Middlebox#
The figure below depicts the high-level architecture components and interactions that achieve visibility of TLSv1.3 traffic using active break and inspect middleboxes. In this approach, each TLS connection from a TLS client is terminated at the middlebox. The middlebox then initiates a second TLS connection to the target TLS server. The middlebox copies the TLS traffic from the client-facing TLS connection to the server-facing TLS connection while passing the clear text of the traffic to the Real-time Analytics Platform. Finally, the middlebox registers the ephemeral session key for each TLS session with the Key Governance Platform. The post facto analytics platform can retrieve the ephemeral keys by querying the Key Governance Platform using the client random identifier of the TLS session to be decrypted. Additional details for this architecture are available in Section 5.3 of NIST SP 1800-37B: Approach, Architecture, and Security Characteristics.
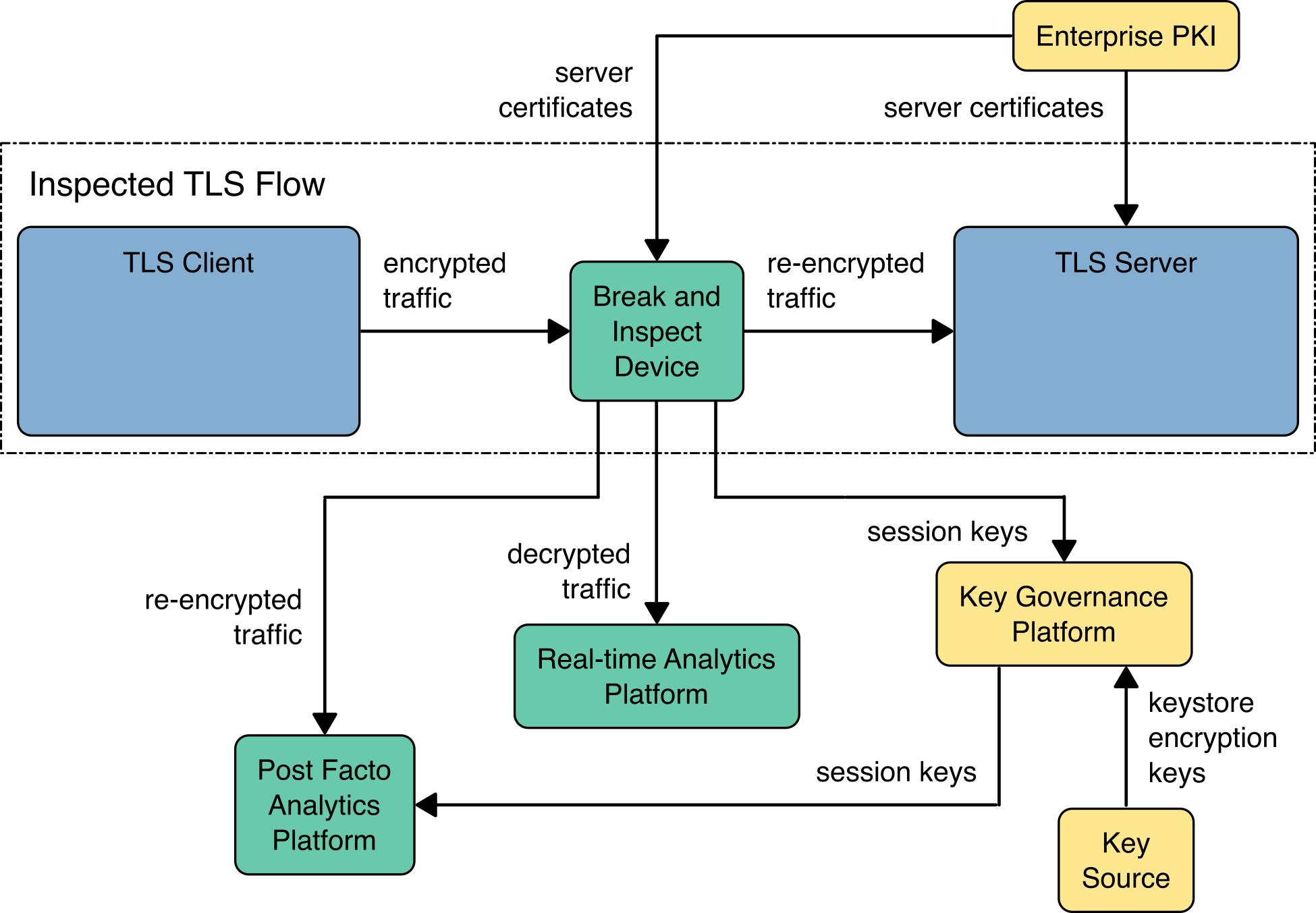
Reference Architecture for Active Break and Inspect Decryption#
The lab has two builds of this reference architecture: one that operates on traffic at the OSI Layer 3 level, and one that operates on the OSI Layer 2 level. In the lab build for the Layer 3 version of this reference architecture, the software or services used for each of the architecture components can be found in the tables below.
Architecture Component |
Collaborator |
Product Information |
|---|---|---|
Architecture Component |
Collaborator |
Product Information |
Enterprise PKI |
DigiCert |
CertCentral Certificate Management Platform |
TLS Client |
Mozilla Firefox Browser |
|
Microsoft Edge Browser |
||
Command-line Email Client & Mozilla Thunderbird |
||
Break and Inspect Device (Layer 3) |
F5 |
BIG-IP SSL Orchestrator Version 17.0.0 build 0.0.22 |
F5 Syslog Receiver / Redis Forwarder Server |
||
TLS Server(s) |
Containerized nginx reverse proxy and Keycloak IdAM application |
|
Containerized nginx reverse proxy and Python test app |
||
Key Governance Platform |
AppViewX |
appviewX Version 2020.3.10 build 55 Virtual Appliance |
Redis database |
||
Real-time Analytics Platform |
NetScout |
nGeniusONE Version 6.3.5 build 2416 |
Omnis Cyber Intelligence (OCI) Version 6.3.5 build 2416 |
||
Post Facto Analytics Platform |
vSTREAM ISNG Version 6.3.5 build 946 |
|
vCYBERSTREAM ISNG Version 6.3.5 build 946 |
||
Key Source |
Thales TCT |
Luna Network HSM T-5000 Firmware: Version 7.11.1 FIPS-validated |
Architecture Component |
Collaborator |
Product Information |
|---|---|---|
Architecture Component |
Collaborator |
Product Information |
Enterprise PKI |
DigiCert |
CertCentral Certificate Management Platform |
TLS Client |
Mozilla Firefox Browser |
|
Microsoft Edge Browser |
||
Command-line Email Client & Mozilla Thunderbird |
||
Break and Inspect Device (Layer 2) |
MIRA |
Encrypted Traffic Orchestration (ETO) Version 3.1.0-2024.11.28-4781 Virtual Appliance |
TLS Server(s) |
Containerized nginx reverse proxy and Keycloak IdAM application |
|
Containerized nginx reverse proxy and Python test app |
||
Key Governance Platform |
AppViewX |
appviewX Version 2020.3.10 build 55 Virtual Appliance |
Redis database |
||
Real-time Analytics Platform |
NetScout |
nGeniusONE Version 6.3.5 build 2416 |
Omnis Cyber Intelligence (OCI) Version 6.3.5 build 2416 |
||
Post Facto Analytics Platform |
vSTREAM ISNG Version 6.3.5 build 946 |
|
vCYBERSTREAM ISNG Version 6.3.5 build 946 |
||
Key Source |
Thales TCT |
Luna Network HSM T-5000 Firmware: Version 7.11.1 FIPS-validated |
Return to Middlebox Architecture. Return to Architecture and Builds.