Scenario 3.3: Command and Control#
Purpose#
Scan network traffic content for known command-and-control or exfiltration protocols.
Description#
This demonstration shows how decrypted traffic can be utilized to identify, collect, and report on Command-and-Control activity on the network. A traffic generation script produced sample Command-and-Control traffic over the network.
Procedure#
Use script3.3 to make a request to an HTTP server configured to simulate Command and Control traffic.
Observe the detection of the traffic as indicative of Command and Control activity in NetScout’s Security Events Center.
Expected Outcome#
The traffic is detected as potentially indicative of a Command and Control attack by NetScout’s internal IDS.
Passive |
Active |
||||||
|---|---|---|---|---|---|---|---|
Bounded Life-Time |
Exported Session Key |
Break & Inspect (Mira) |
Break and Inspect (F5) |
||||
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Screenshots#
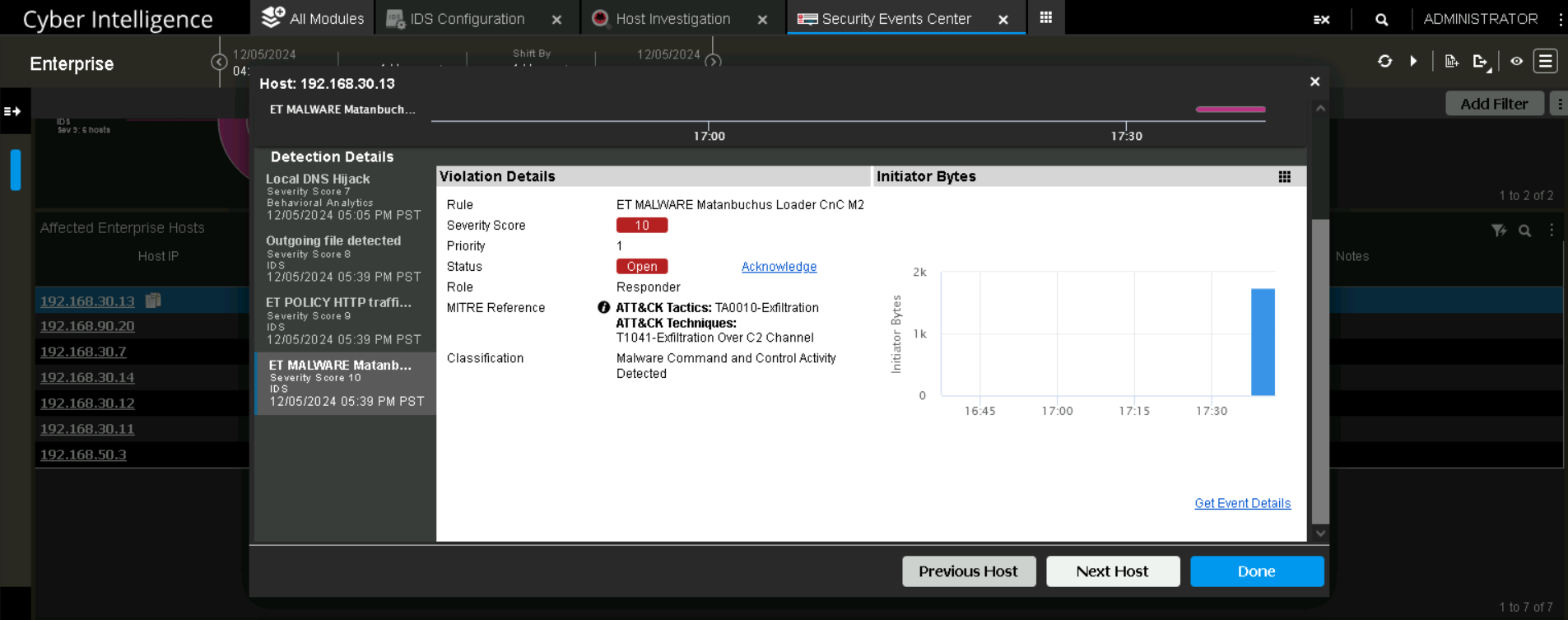
Detection of potential Command and Control attack.#