Scenario 4.1: Outdated Protocols#
Purpose#
Identify and report on the use of outdated protocols. (and/or ‘practices’).
Description#
This demonstration shows how decrypted traffic can be utilized to identify, collect, and report on the use of outdated protocols in network traffic. A traffic generation script was used to utilize outdated protocols on the network.
Procedure#
Use script4.1 to generate TLS1.2 traffic.
Observe the identification of the traffic as TLS1.2 in NetScout’s Packet Analysis tool.
Expected Outcome#
The traffic is identified as TLS1.2 in NetScout.
Passive |
Active |
||||||
|---|---|---|---|---|---|---|---|
Bounded Life-Time |
Exported Session Key |
Break & Inspect (Mira) |
Break and Inspect (F5) |
||||
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Screenshots#
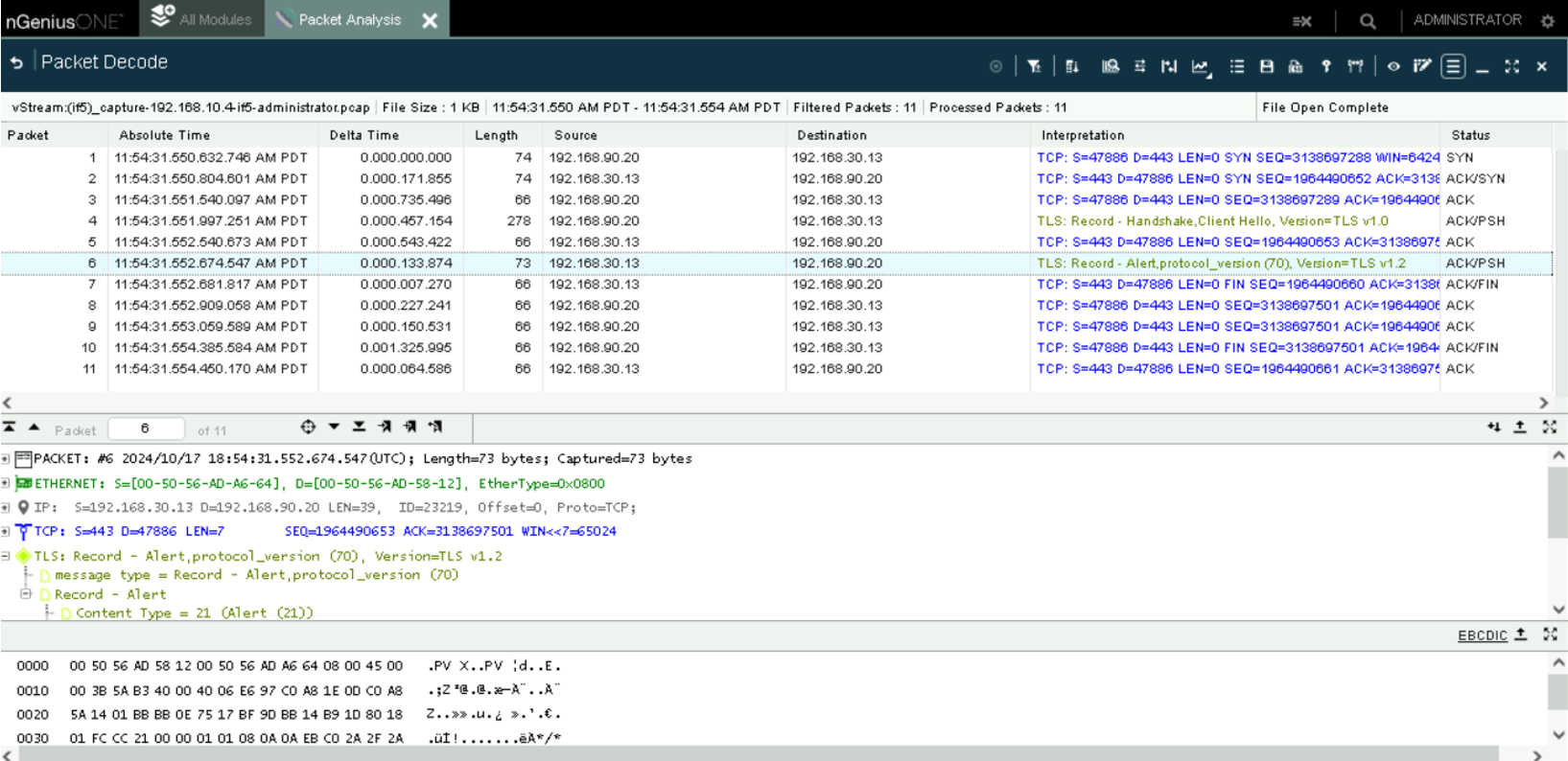
TLS1.2 traffic.#