Scenario 1.1: Expired TLS Certificates#
Purpose#
Identify failed network traffic due to expired TLS PKI certificates (Layer 4).
Description#
This demonstration shows how decrypted traffic can be used to report on expired TLS certificates and provide a path towards speedy remediation.
Procedure#
Assign an almost expired certificate to one of the proxy machines.
Wait for the expiration date to elapse.
(MIRA) Observe the detection of the expired certificate in Mira’s Session Log.
(F5) Observe the detection of the expired certificate in F5’s Certificate Management.
Expected Outcome#
The expiry of the certificate is visible in the user interface for the decryptor.
Passive |
Active |
||||||
|---|---|---|---|---|---|---|---|
Bounded Life-Time |
Exported Session Key |
Break & Inspect (Mira) |
Break and Inspect (F5) |
||||
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Real-Time |
Post-Facto |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Pass |
Screenshots#
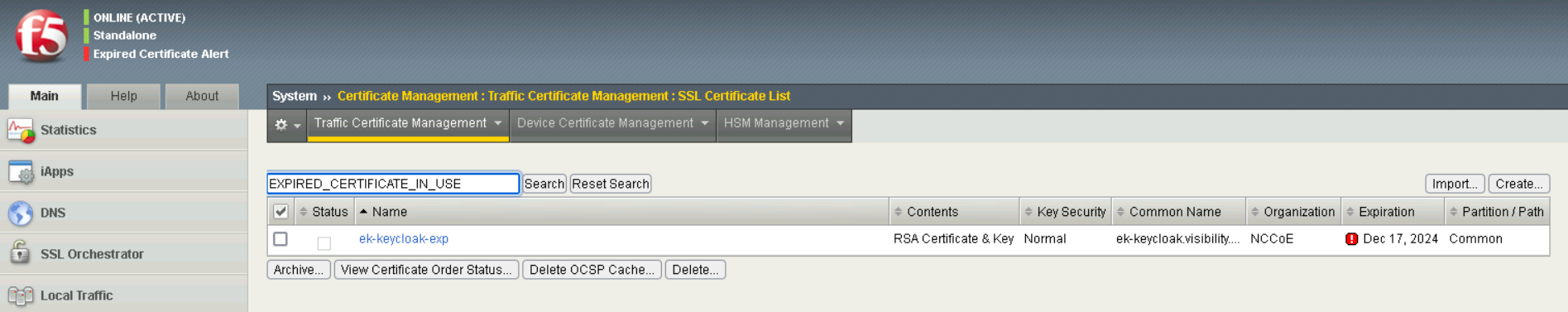
F5 showing expired certificates in its list of certificates.#
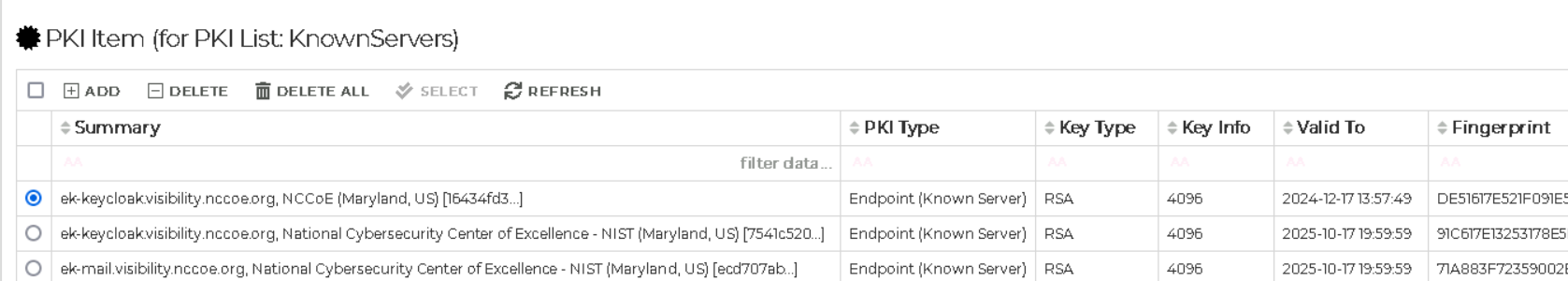
Mira showing expired certificates in the context of a network flow.#
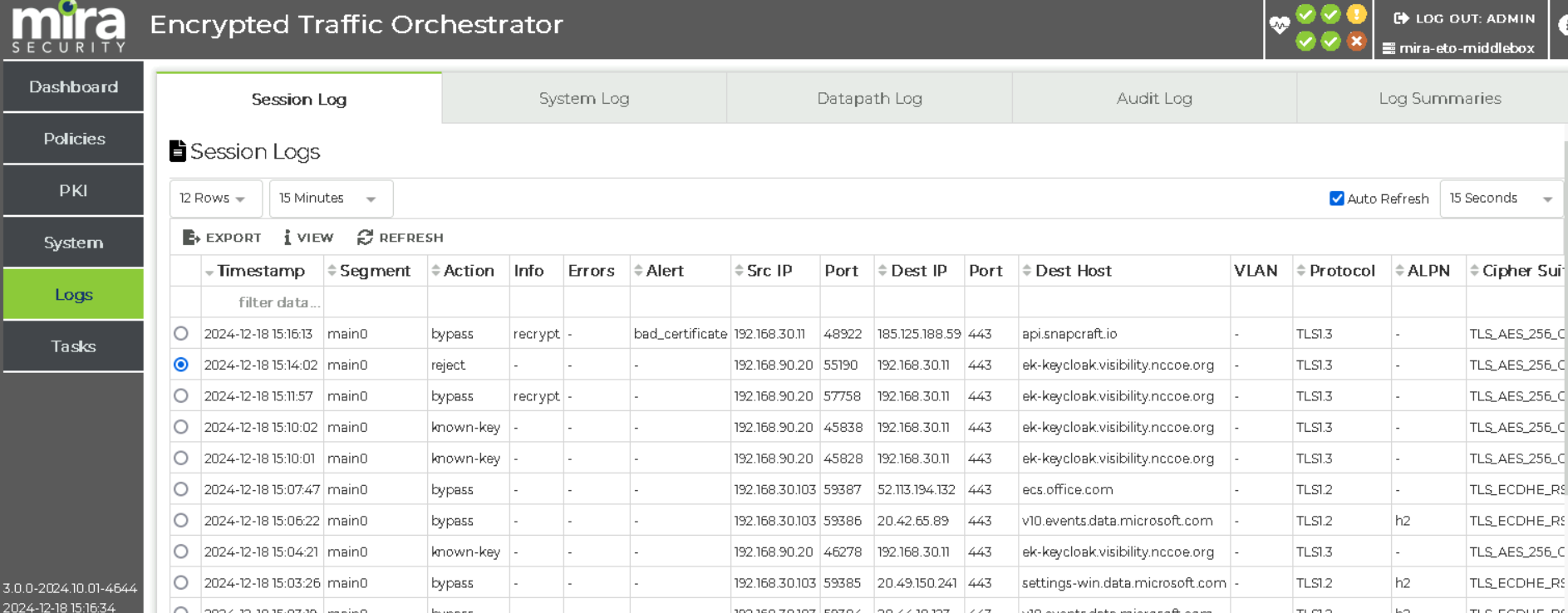
Mira rejecting traffic based on the expiry of the certificate.#