Communication
Contemporary mobile devices contain integrated hardware components to support a variety of I/O mechanisms. While some of the communication mechanisms are wireless (i.e., cellular, WiFi, Bluetooth, GPS, NFC), others require a physical connection (i.e., power and synchronization cable, SIM, external storage). As seen in the figure below, each of these different wireless and wired device communication mechanisms exposes the device to a distinct set of threats and must be secured or the overall security of the device may be compromised. The following sections provide a brief overview of each communication mechanism.
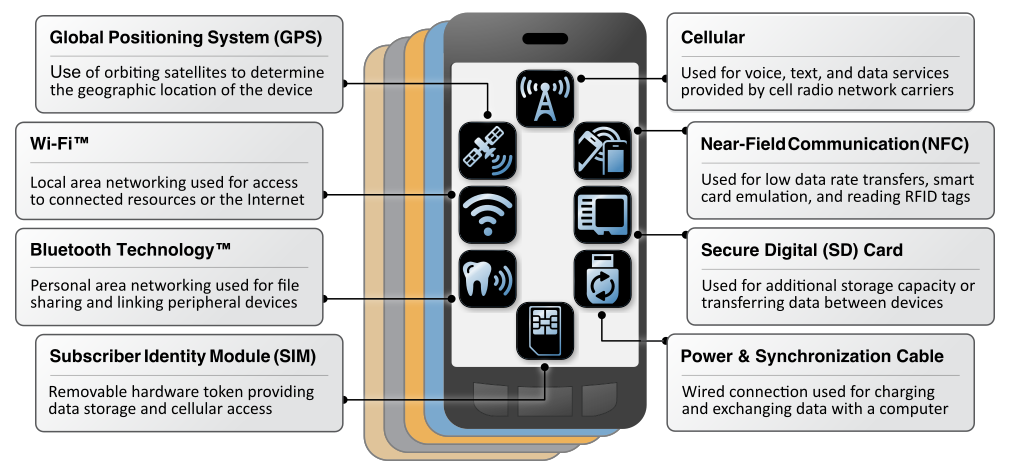 Mobile Device Communication Mechanisms
Mobile Device Communication Mechanisms
Subscriber Identity Module (SIM)
This removable hardware token is colloquially referred to as the Subscriber Identity Module (SIM) card, although current standards use the term Universal Integrated Circuit Card (UICC). This System on a Chip (SoC) houses the subscriber identity (i.e., International Mobile Subscriber Identity), pre-shared cryptographic keys, and configuration information needed to obtain access to cellular networks. The UICC is essentially a smartcard that runs a Java application known as the Universal Subscriber Identity Module (USIM), which is used to run a set of applications that control the phone’s access and authentication with the MNO’s cellular networks and roaming partners. It is possible to develop and run other applications on the Java Card platform, such as games and mobile payment applications.
As of the writing of this report, a technology called Embedded SIM (eSIM) is being integrated into some mobile devices. eSIMs will allow MNOs to remotely provision subscriber information during initial device setup, and allow the remote changing of subscription from one MNO to another. While this technology may radically change the way mobile devices are provisioned on the carrier network and therefore introduces a new set of threats.
Cellular Air Interface
The cellular air interface is arguably the defining networking interface for modern mobile devices. Initial cellular systems, such as second generation (2G) Global System for Mobile Communications (GSM) and third generation (3G) Universal Mobile Telecommunications System, were modeled after the traditional wireline circuit-switched telephone system. Each call was provided with a dedicated circuit providing a user making a telephone call with a baseline guarantee of service. In contrast, newer fourth generation (4G) Long Term Evolution (LTE) networks were designed to utilize a packet-switched model for both data and voice. An LTE network provides consistent IP connectivity between an end user's mobile device and IP-based services on the packet data network (PDN).
There are many cellular network types, each with its own air interface standards. The cellular air interface is the technical term for the radio connection between a mobile device and the cellular tower. This air interface can generally communicate with many types of base stations (e.g., cellular towers) which come in many sizes and types — cellular repeater / relay nodes, and even other handsets.
MNOs strive to run high availability “carrier grade” services that operate over the air interface at the network level, and can integrate with other systems they operate. These services may include circuit switched calling, VoLTE (Voice over LTE), Unstructured Supplementary Service Data (USSD), integrated voicemail with notifications, and messaging (e.g., Short Messaging Service (SMS)). Carrier-grade messaging services are commonly referred to as text messages, but include SMS, the extension to SMS known as Multimedia Messaging Service (MMS), and the new Rich Communication Services (RCS). USSD is an aging method for establishing a real-time session with a service or application to quickly share short messages. Although not common within the United States, USSD is used in emerging markets for a number of services, including mobile banking.
For additional discussion of LTE security architecture see NIST SP 800-187 – Guide to LTE Security.
WiFi
WiFi is a wireless local area network (WLAN) technology based on the IEEE 802.11 series of standards. WiFi is used by most mobile devices as an alternative to cellular data channels, or even the primary data egress point in WiFi-only mobile devies. WLANs typically consist of a group of wireless devices within a contained physical area, such as an apartment, office, or coffee shop, but more expansive enterprise or campus deployments are also common. While not guaranteed, campus or enterprise deployments are more likely to implement security features such as WPA2 encryption. Smartphones, laptops, and other devices utilizing WiFi often need to connect back to a central wireless access point (APs), but may work in a device-to-device ad hoc mode.
Readers looking for additional guidance for the installation, configuration, deployment, and security of WiFi can see NIST SP 800-153 – Guidelines for Securing Wireless Local Area Networks or SP 800-97 – Establishing Wireless Robust Security Networks: A Guide to IEEE 802.11i.
Global Navigation Satellite System (GNSS)
A GNSS provides worldwide geo-spatial positioning via the global positioning system (GPS), which uses line of sight communication with a satellite constellation in orbit to help a handset determine its location. These systems run independently of cellular networks. The US Federal Government operates a GPS constellation, although mobile devices may use other systems (e.g., GLONASS, Galileo). It should be noted that the GPS system is not the only way for a mobile device to identify its location. Other techniques include Wi-Fi assisted positioning, which leverages databases of known service set identifiers (SSIDs) and geolocation of IP addresses.
Bluetooth
Bluetooth is a short-range wireless communication technology. Bluetooth technology is used primarily to establish wireless personal area networks (PANs). Bluetooth technology has been integrated into many types of business and consumer devices including cell phones, laptops, automobiles, medical devices, printers, keyboards, mice, headphones, and headsets. This allows users to form ad hoc networks between a wide variety of devices to transfer data.
For additional information about Bluetooth security, see NIST SP 800-121 Revision 2 – Guide to Bluetooth Security.
Near Field Communication (NFC)
NFC uses radio frequency emissions to establish low throughput, short-range communication between NFC-enabled devices. It is typically optimized for distances of less than 4 inches, but can potentially operate at and pose a threat at much greater distances. NFC is based on the radio frequency identification (RFID) set of standards. Mobile payment technology relies on NFC, which has led to NFC’s increasing visibility in recent years as newer mobile wallet technologies are being deployed on a large scale. The use of NFC for financial transactions make it attractive to criminal attackers with the goal of financial gain.
For additional information on the security challenges associated with RFID, refer to NIST SP 800-98 – Guidelines for Securing Radio Frequency Identification (RFID) Systems.
Secure Digital (SD) Card
The SD card standard comprises various form factors that offer different performance ratings and storage capacities. SD cards are typically used to expand the storage capacity of mobile devices to store data such as photos, videos, music, and application data. SD cards are not integrated into every mobile device, although the use of SD cards is particularly popular in developing nations where built-in storage may be uncommon.
Power & Synchronization Port
The power and synchronization port on a mobile device is most often used to charge a mobile device, and may take the form of Universal Serial Bus (USB) Type-C, Micro-USB, Apple Lightning, or Apple 30 pin. The cable is also used to carry data to, or access the device from, another information system. Use cases include data synchronization with or backup to a PC, or provisioning into an Enterprise Mobility Management system. This cable may also be used to charge another device in some circumstances. Because of this dual use of power and data, this interface is used as a vector for a number of attacks.