Appendix F. Dataflow Analysis#
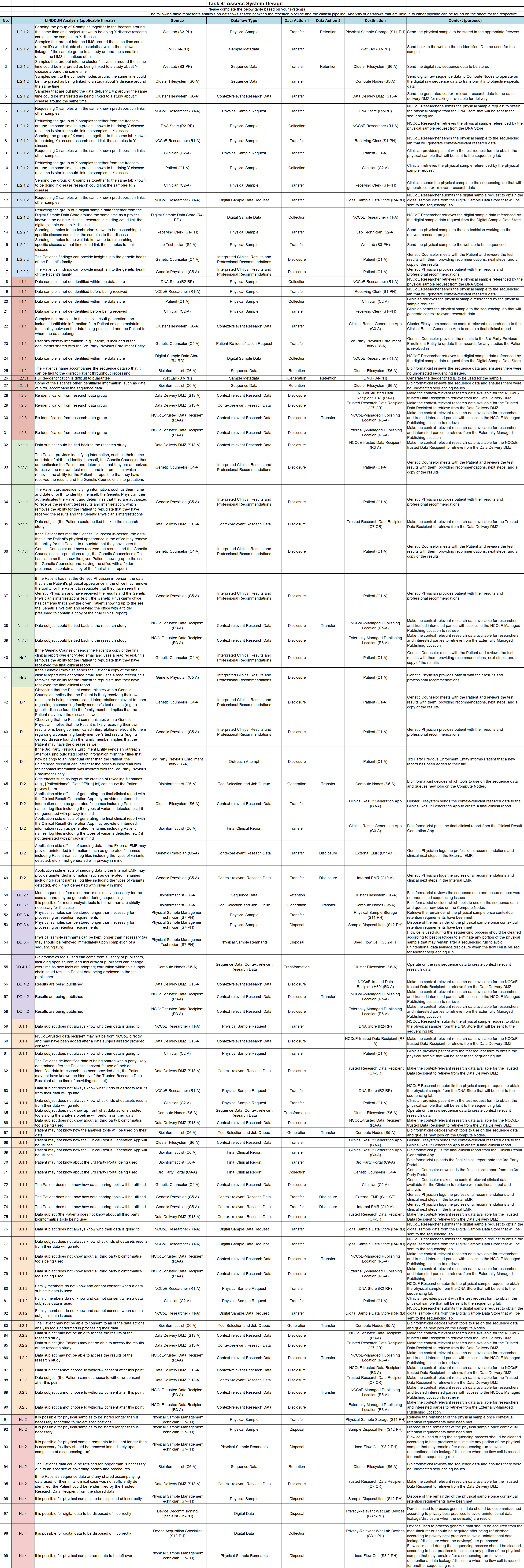
This appendix presents the LINDDUN and PANOPTIC analyses for the complete example. The LINDDUN dataflow analysis was initially broken down in a manner similar, but not identical, to the dataflow diagrams, with separate analysis tables for the clinical and research use cases together with a table for their shared dataflows. The individual tables were integrated into a single table that was then sorted on the LINDDUN threat families. Separate PANOPTIC threat action mappings were generated for the clinical and research use cases and used to identify attack scenarios.
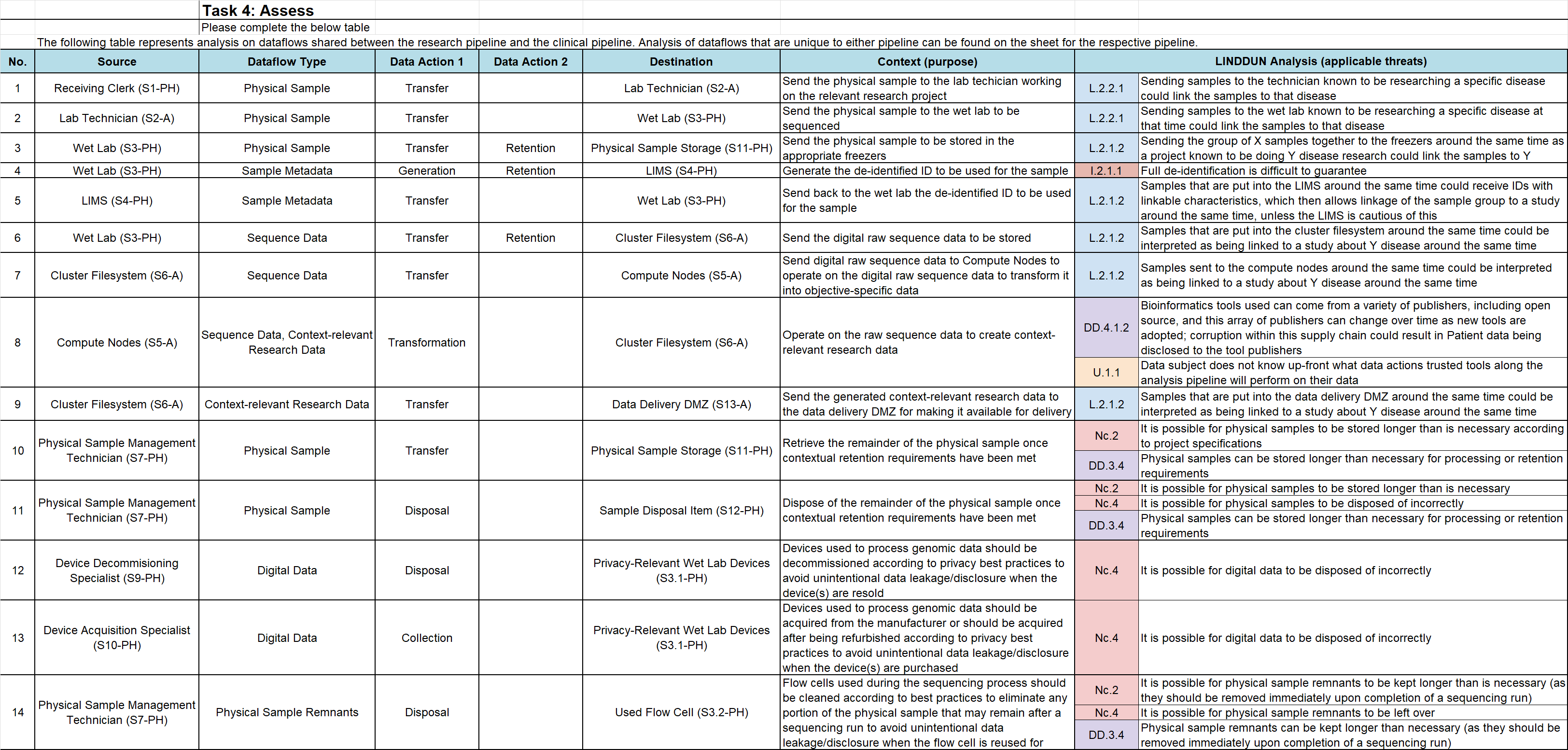
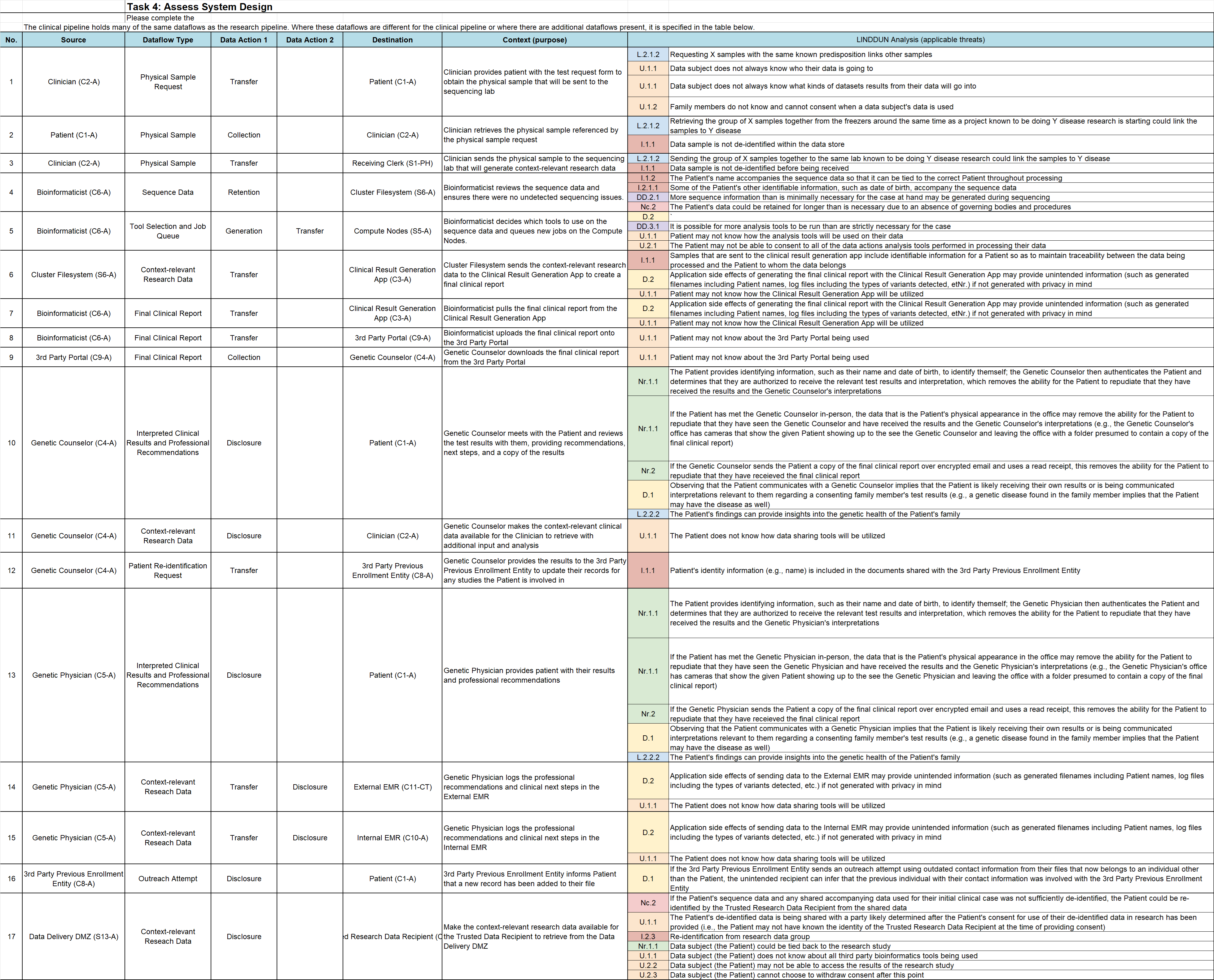
Dataflow Analysis for Clinical Use Case#
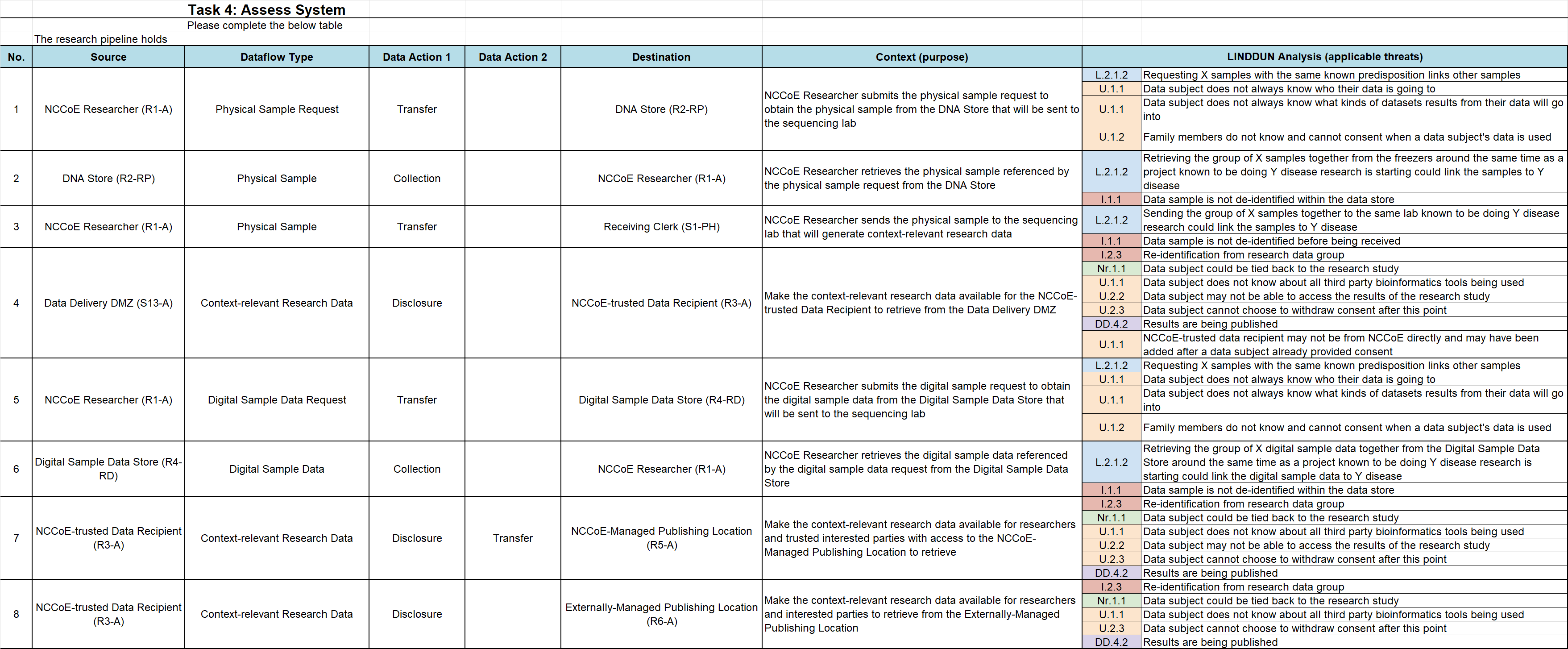
Dataflow Analysis for Research Use Case#
Integrated and Sorted Dataflow Analysis#
PANOPTIC Privacy Activities Mapping for Clinical Use Case#


PANOPTIC Privacy Activities Mapping for Research Use Case#


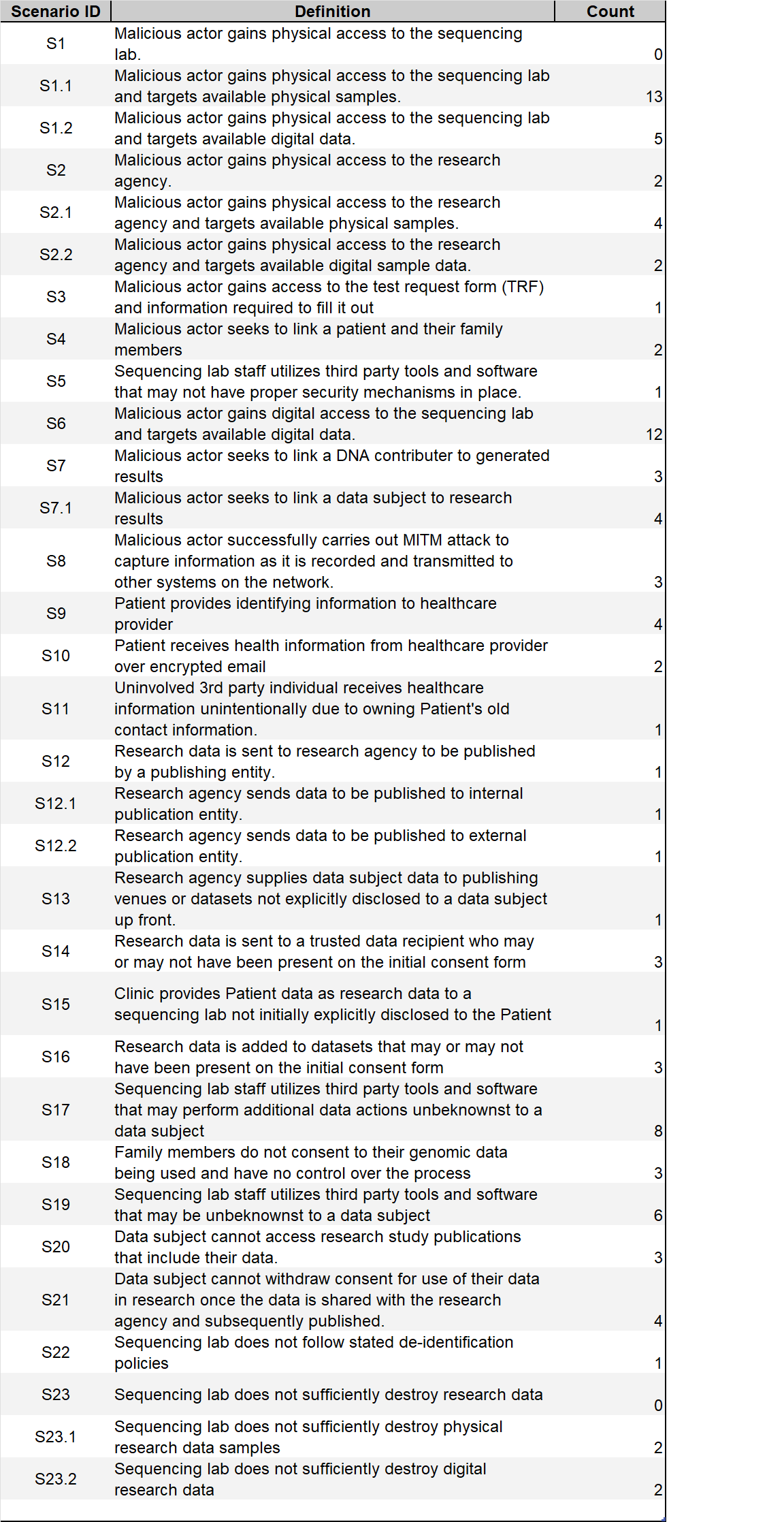
Scenarios#