Identity Proofing Overview
This section is normative.
This section provides an overview of the identity proofing and enrollment process, as well as requirements to support the resolution, validation, and verification of the identity claimed by an applicant. It also provides guidelines on additional aspects of the identity proofing process. These requirements are intended to ensure that the claimed identity exists in the real world and that the applicant is the individual associated with that identity.
These guidelines provide multiple methods by which resolution, validation, and verification can be accomplished, as well as multiple types of identity evidence that support the identity proofing process. CSPs and organizations SHOULD provide options when implementing their identity proofing services and processes to promote access for applicants with different means, capabilities, and technologies. These options SHOULD include accepting multiple types and combinations of identity evidence, supporting multiple data validation sources, enabling multiple methods for verifying identity, providing multiple identity proofing types, and offering exception handling for applicants (e.g., trusted referees, applicant references).
CSPs SHALL evaluate the risks associated with each identity proofing option offered (e.g., identity proofing types, validation sources, assistance mechanisms) and implement mitigating fraud controls, as appropriate. At a minimum, CSPs SHALL design each option such that the options provide comparable assurance in aggregate.
Requirements are typically expressed in these guidelines as responsibilities of the CSP unless otherwise noted. CSP requirements may be performed by a single entity or may include several component services so that all CSP responsibilities are fulfilled.
Identity Proofing and Enrollment
The intent of identity proofing is to ensure that the applicant involved in the identity proofing process is who they claim to be to a stated level of confidence. This document presents a three-step process for CSPs to identity-proof applicants at designated assurance levels. The first step is identity resolution, which consists of collecting appropriate identity evidence and attribute information to determine whether the applicant is a unique identity in the population served by the CSP and a real-life person. The second step is identity validation, which confirms the authenticity, accuracy, and validity of the evidence and attribute information collected in the first step. The third step is identity verification, which confirms that the applicant presenting the identity evidence is the same individual to whom the evidence was issued. In most cases, upon successfully identity proofing an applicant to the designated IAL, the CSP establishes a unique subscriber account for the applicant (now a subscriber in the identity service), which allows one or more authenticators to be bound to the proven identity in the account.
Identity proofing can be part of an organization’s business processes to determine the suitability or entitlement to a benefit or service, though such determinations are outside of the scope of these guidelines.
Process Flow
This subsection is informative.
Figure 1 provides an illustrative example of the three-step identity proofing process.
Fig. 1. Identity proofing process
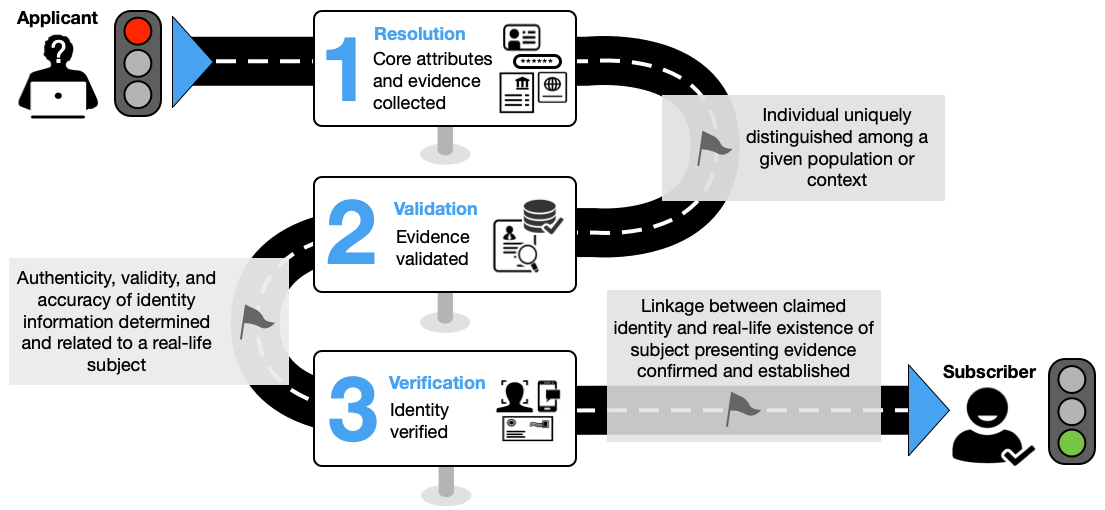
The following steps present a common workflow example of remote unattended identity proofing and are not intended to represent a normative processing workflow model.
-
Resolution
- The CSP collects one or two pieces of identity evidence of appropriate strength.
- The CSP collects any additional core attributes, as needed, from the applicant to supplement those contained in the presented identity evidence.
-
Validation
- The CSP confirms that the presented evidence is authentic, accurate, and valid.
- The CSP validates the attributes obtained in step 1 by checking them against authoritative or credible validation sources, as described in Sec. 2.4.2.4.
-
Verification
- The CSP employs an approved identity verification process to confirm that the applicant is the genuine owner of the presented identity evidence.
-
Enrollment
Upon the successful completion of the three identity proofing steps, a notification of proofing is sent to a validated address, and the applicant can be enrolled into a subscriber account with the CSP, as described in Sec. 5. A subscriber account includes at least one validated address (e.g., phone number, mailing address) that can be used to communicate with the subscriber about their account. Additionally, one or more authenticators are bound to the proven identity in the subscriber account.
Identity Proofing Roles
Different individuals can play different roles within the proofing process. To support the consistent implementation of these guidelines, the following identity proofing roles are defined:
- Proofing agent: An agent of the CSP who is vetted and trained to attend on-site or remote identity proofing sessions and make limited, risk-based decisions (e.g., visually inspecting identity evidence and determining it has not been altered). See Sec. 3.13 for minimum training requirements for proofing agents.
- Trusted referee: An agent of the CSP, a third-party service, or a relying party (RP) who is vetted and trained to make risk-based decisions regarding an applicant’s identity proofing case when that applicant is unable to meet the expected requirements of a defined IAL proofing process. Requirements for trusted referees are contained in Sec. 3.15.1. In contrast to proofing agents, trusted referees receive additional training and resources to support exception handling scenarios, including when applicants do not possess the required identity evidence or the attributes on the evidence do not all match the claimed identity (e.g., due to a recent name or address change).
- Applicant reference: A representative of the applicant who can vouch for the identity of the applicant, specific attributes related to the applicant, or conditions relative to the context of the individual (e.g., emergency status, homelessness). An applicant reference does not act on behalf of the applicant in the identity proofing process but can support claims of identity. Requirements for applicant references are contained in Sec. 3.15.3.
- Process assistant: An individual who provides support services (e.g., translation, transcription, or accessibility support) to assist the applicant in the identity proofing process but does not support decision-making or risk-based evaluation. Since the process assistant is not involved in decision-making there are no requirements in these guidelines for this role.
CSPs SHALL identify which of the above roles are applicable to their identity service and SHALL provide training and support resources consistent with the requirements and expectations provided in Sec. 3.
Identity Proofing Types
For the purposes of this document, identity proofing types are defined by the combination of technologies, communication channels, and identity proofing roles employed by a CSP. Identity proofing types are characterized based on two factors: where the identity proofing takes place and whether the process is attended by an agent of the CSP.
- Remote unattended identity proofing: Identity proofing conducted where the resolution, validation, and verification processes are completely automated, and interaction with a proofing agent or trusted referee is not required. The location and devices used in the proofing process are not controlled by the CSP.
- Remote attended identity proofing: Identity proofing conducted where the applicant completes resolution, validation, and verification steps through a secure video session with a proofing agent or trusted referee. The location and devices used in the proofing process are not controlled by the CSP.
- On-site unattended identity proofing: Identity proofing conducted where an individual interacts with a controlled workstation or kiosk, but interaction with a proofing agent or trusted referee is not required. The process is fully automated but at a physical location and on devices controlled by the CSP.
- On-site attended identity proofing: Identity proofing conducted in a physical setting where the applicant completes the entire identity proofing process (i.e., resolution, validation, and verification) in the presence of a proofing agent or trusted referee. The proofing agent or trusted referee can be co-located with the user or interact with the user via a kiosk or device. The physical location and devices are controlled by the CSP.
The requirements at each assurance level are structured to allow CSPs to implement different combinations of identity proofing types to meet the requirements of different assurance levels, as appropriate. CSPs SHOULD offer the combination of identity proofing types that best addresses the needs of the populations served by their identity service and the risk posture of the RPs that use their service.
Core Attributes
The identity proofing process involves the presentation and validation of the minimum attributes necessary to accomplish identity proofing, including what is needed to complete resolution, validation, and verification. The CSP determines and documents the set of attributes that it considers to be core attributes, as specified in Sec. 3.1. CSPs SHALL include a government identifier1 and SHOULD include the following in their set of core attributes for identity proofing at any IAL:
- First name: The applicant’s given name.
- Middle name or initial: The applicant’s middle name or initial, as applicable.
- Last name: The applicant’s last name or family name, as appropriate.
- Date of birth: The date on which the applicant was born.
- Physical or digital address: A physical (i.e., mailing address) or digital (e.g., phone number or email) address at which the applicant can receive communications related to the proofing process.
Additional attributes MAY be added to these as required by the CSP and RP. The CSP and RP SHALL document all core attributes in trust agreements and practice statements. Following a privacy risk assessment, a CSP MAY request additional attributes that are not required to complete identity proofing, but that may support other RP business processes. See Sec. 3.3 for details on privacy requirements for requesting additional attributes.
Identity Resolution
Identity resolution involves the CSP’s collection of the minimum amount of identity evidence and attribute information that is needed for identity proofing and to distinguish a unique identity in the population served. Identity resolution is the starting point in the overall identity proofing process, including the initial detection of potential fraud.
Identity Evidence and Attributes
Identity evidence is information or documentation that supports the real-world existence of the claimed identity. Identity evidence may be physical (e.g., a driver’s license) or digital (e.g., a mobile driver’s license or digital assertion).
Identity evidence collection supports the identity validation process and consists of two steps: 1) the presentation of identity evidence by the identity proofing applicant to the CSP and 2) the determination by the CSP that the presented evidence meets the applicable strength requirements.
Evidence Strength Requirements
This section defines the requirements for identity evidence at each strength. The strength of a piece of identity evidence is determined by:
- The level of rigor associated with its issuance process
- The ability to be validated to a given level of confidence, including accuracy and authenticity checks
- The ability to support one or more of the identity verification methods presented in Sec. 2.5.1
Appendix A of this document provides a non-exhaustive list of possible evidence types grouped by strength.
Fair Evidence Requirements
To be considered FAIR, identity evidence SHALL meet all of the following requirements:
- There is a reasonable expectation that the issuing source of the evidence confirmed the claimed identity by following formal procedures designed to provide assurance that the claimed identity is associated with the subject, such as evidence issued by financial institutions that have customer identity verification obligations under the Customer Identification Program (CIP) rule or procedures for establishing a mobile phone account with a mobile network operator (MNO).
- The evidence has an issuance process that results in the delivery of the evidence to the person to whom it relates, such as delivery to a postal address, issuance in person, or through a protected remote provisioning process.
- The evidence contains the name of the claimed identity.
- The evidence contains at least one reference number, a facial image or other biometric characteristic, or sufficient attributes to uniquely identify the person to whom it relates.
- The evidence contains physical (e.g., security printing, optically variable features, holograms) or digital (e.g., digitally signed assertions, addressable SIM or ESIM) security features that make it difficult to reproduce.
- Core attributes on the evidence can be validated against information held by an authoritative or credible source, as described in Sec. 2.4.2.4.
- The evidence can be validated through an approved method, as provided in Sec. 2.4.2.2.
- The evidence can support the identity verification process, as described in Sec. 2.5.1.
Strong Evidence Requirements
In order to be considered STRONG, identity evidence SHALL meet all of the following requirements:
- There is a reasonable expectation that the issuing source of the evidence confirmed the claimed identity by following written procedures (e.g., identity proofing at IAL2 or above) designed to provide assurance that the claimed identity is associated with the subject. Additionally, these procedures are subject to recurring oversight by regulatory or publicly accountable institutions, such as states, the Federal Government, and some regulated industries.
- The evidence has an issuance process that results in the delivery of the evidence to the person to whom it relates, such as delivery to a postal address, issuance in person, or through a protected remote provisioning process.
- The evidence contains the name of the claimed identity.
- The evidence contains a reference number or other attributes that uniquely identify the person to whom it relates.
- The evidence contains a facial image or other biometric characteristic of the person to whom it relates.
- The evidence contains physical (e.g., security printing, optically variable features, holograms) or digital security (e.g., digitally signed assertions, addressable SIM or ESIM) features that make it difficult to reproduce.
- Core attributes on the evidence can be validated against information held by authoritative or credible sources, as described in Sec. 2.4.2.4.
- The evidence can be validated through an approved method, as provided in Sec. 2.4.2.2.
- The evidence can support the identity verification process, as described in Sec. 2.5.1.
Superior Evidence Requirements
In order to be considered SUPERIOR, identity evidence SHALL meet all of the following requirements:
- The issuing source of the evidence confirmed the claimed identity by following written procedures (e.g., identity proofing at IAL2 or above) designed to enable it to have high confidence that the claimed identity is associated with the subject. Additionally, these procedures are subject to recurring oversight by regulatory or publicly accountable institutions, such as states, the Federal Government, and some regulated industries.
- The identity evidence contains attributes and data objects that are cryptographically protected and can be validated using approved cryptography through verification of a digital signature applied by the issuing source.
- The issuing source had the subject participate in an attended enrollment and identity proofing process that confirmed their physical existence.
- The evidence has an issuance process that results in the delivery of the evidence to the person to whom it relates, such as delivery to a postal address, issuance in person, or through a protected remote provisioning process.
- The evidence contains the name of the claimed identity.
- The evidence contains at least one reference number that uniquely identifies the person to whom it relates.
- The evidence contains a facial image or other biometric characteristic of the person to whom it relates.
- The evidence contains physical (e.g., security printing, optically variable features, holograms) or digital security (e.g., digitally signed assertions, addressable SIM or ESIM) features that make it difficult to reproduce.
- The evidence can be validated through an approved method, as provided in Sec. 2.4.2.2.
- The evidence can support the identity verification process, as described in Sec. 2.5.1.
Identity Evidence and Attribute Validation
The goal of identity evidence validation is to determine that the collected identity evidence is genuine and valid. The goal of attribute validation is to confirm the accuracy of all the core attributes.
This document uses the term “valid” to recognize that evidence can remain a useful means to prove identity, even if it is expired or was issued outside of a determined time frame. CSPs define their policy for addressing expired evidence as part of the CSP practice statement described in Sec. 3.1, and RPs determine whether this is acceptable for accessing their online services.
Identity evidence validation involves examining the presented evidence to confirm that it is authentic (i.e., not forged or altered), accurate (i.e., the information on the evidence is correct), and valid (i.e., unexpired or within the CSP’s defined timeframe for issuance or expiration). Attribute validation involves confirming the accuracy of the core attributes, whether obtained from presented evidence or self-asserted. The following subsections provide acceptable methods for evidence and attribute validation.
Evidence Validation
The CSP SHALL validate the authenticity, accuracy, and validity of presented evidence by confirming that:
- The evidence is in the correct format and includes complete information for the identity evidence type
- The evidence does not show signs of being counterfeit or tampered with
- The evidence contains physical or digital security features
- The core attributes and data fields necessary to determine authenticity on the evidence are accurate
Evidence Validation Methods
Acceptable methods for validating presented evidence are:
- Visual and tactile inspection by trained personnel for on-site identity proofing
- Visual inspection by trained personnel for remote identity proofing
- Automated document validation processes using appropriate technologies
- Cryptographic verification of the source and integrity of digital evidence or attribute data objects
For some digital evidence (e.g., MNO/phone accounts), there is not a physical piece of evidence that can be validated visually or physically. Authenticity is confirmed by validating the identity attributes associated with that account and phone number with an issuing or credible source, such as by validating a digitally signed assertion from the issuer or querying an attribute validation service with access to that account information.
Attribute Validation
The CSP SHALL validate all core attributes (Sec. 2.2), whether obtained from identity evidence or self-asserted by the applicant, with an authoritative or credible source (Sec. 2.4.2.4).
Validation Sources
The CSP SHALL use authoritative or credible sources that meet the following criteria.
An authoritative source is the issuing source of identity evidence or attributes or has direct access to the information maintained by issuing sources. Examples of issuing sources include state departments of motor vehicles for driver’s license data and the Social Security Administration for Social Security cards and numbers. An example of an authoritative source that provides or enables direct access to issuing sources is the American Association of Motor Vehicle Administrators’ Driver’s License Data Verification (DLDV) Service.
A credible source has access to attribute information that can be traced to an authoritative source or maintains identity attribute information obtained from multiple sources that is correlated for accuracy, consistency, and currency. Credible sources are subject to regulatory oversight (e.g., the Fair Credit Reporting Act).
Identity Verification
The goal of identity verification is to establish the linkage between the claimed validated identity and the real-life applicant engaged in the identity proofing process to a specified level of confidence. In other words, verification provides assurance that the applicant presenting the evidence is the rightful owner of that evidence.
Identity Verification Methods
The CSP SHALL verify the linkage between the claimed identity to the applicant engaged in the identity proofing process through one or more of the following methods.
- Confirmation code verification: The individual is able to demonstrate control of a piece of identity evidence through the return of a confirmation code, consistent with the requirements specified in Sec. 3.8.
- Authentication and federation protocols: The individual is able to demonstrate control of a digital account (e.g., online bank account) or signed digital assertion through the use of authentication or federation protocols. This can be done in person, through presentation of the credential to a device or reader, or during a remote identity proofing session.
- Transaction verification: An individual is able to demonstrate control of a piece of evidence by returning a value based on a microtransaction made between the CSP and the issuing source of the evidence (e.g., a micro-deposit to verify ownership of a financial account).
- Visual facial image comparison — on-site attended: The proofing agent and applicant interact directly during the identity proofing process. The proofing agent performs a visual comparison of the facial image presented on identity evidence to the face of the applicant engaged in the identity proofing event.
- Visual facial image comparison — remote attended or remote unattended: The proofing agent performs a visual comparison of the facial image presented on identity evidence or stored by the issuing source to the facial image of the applicant engaged in the identity proofing event. The proofing agent may interact directly with the applicant during some or all of the identity proofing process or may conduct the comparison at a later time using a captured video or photograph and the uploaded copy of the evidence.
- Automated biometric comparison: Automated biometric comparison (e.g., facial recognition or other fully automated algorithm-driven biometric comparison) can be performed for onsite or remote identity proofing events. The facial image or other biometric characteristic (e.g., fingerprints, palm prints, iris and retina patterns, voiceprints, vein patterns) on the identity evidence or stored in authoritative records is compared to the equivalent biometric sample collected from the applicant during the identity proofing event.
Knowledge-based verification (KBV) or knowledge-based authentication SHALL NOT be used for identity verification.
-
A government identifier is a unique identifier that is associated with the applicant in government records (e.g., Social Security number, driver’s license number, passport number). ↩